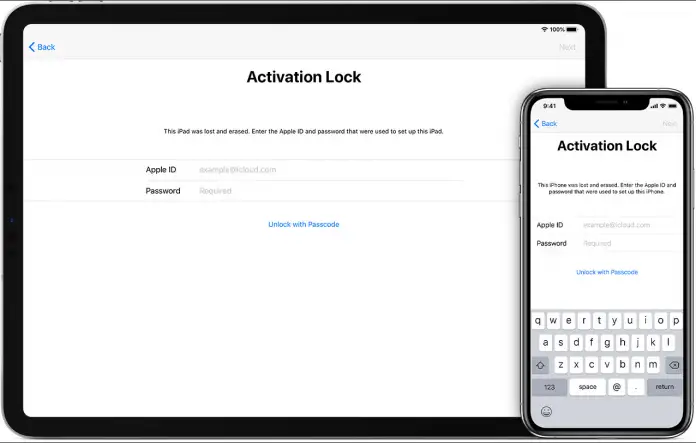
Despite the fact that iPhones are supposed to be the most secure smartphones in the world, in some respects, they are still inferior to Android devices. Whether you have the cheapest Xiaomi or the most expensive Galaxy Fold, they won’t be stolen from you via iCloud.
But the iPhone can be. Obviously, several factors have to come together for this to happen, but, no matter how you look at it, it’s a possibility. So, when we received probably the tenth complaint since the beginning of the year about iPhone remote locking via iCloud, we decided that this topic needed to be addressed.
What to do if your iPhone was blocked via iCloud
One of the most common methods of fraud looks like this: They steal the user’s iCloud account data, login, untie the iPhone or iPad tied to their account, tie it to their account, and demand a ransom by sending a message. Of course, there are exceptions, but a little bit about them is below.
Of course, the scammer doesn’t physically possess the device, so as a rule, he demands a ransom. The main thing here is not to twist it. After all, if they ask for little, they will be fooled, and if they ask for a lot, victims may refuse. Also, for fraudsters, it’s very important to give the victim a strictly fixed time so that the victim has no time to think things over and pay the ransom.
But how can a fraudster get access to your iCloud account in order to take control of the devices connected to it? In fact, we’re not even talking about hacking. Most likely, either your email data leaked into the Web, or you entered your account credentials yourself in a phishing website or other method, for example, via WhatsApp. Both can happen with equal probability and are virtually impossible if you’re vigilant.
How fraudsters act
Usually, the scammer presses your emotions. First, he gives his victim only a limited amount of time (usually an hour). It seems like a lot. But if the person knows how to act in such situations, the allotted time will not play into the hands of the extortionist. Secondly, he threatens that if the ransom isn’t paid, he will block the device and the owner will be charged a much larger sum, usually saying that you will have to replace the motherboard.
Except that there are usually at least two aspects that allow you to convict fraudsters of lying:
- You can’t lock your iPhone or iPad permanently or in any particular way. Basically, fraudsters can reset the data, but if you had a backup, you may well be able to get back everything that was deleted when you regain control of the device.
- Replacing the motherboard in an iPhone or iPad – at least officially – is impossible. Yes, underground shops will sometimes change motherboards, but there’s generally no point in doing it because there’s an easier way to solve the problem.
How to unlock a blocked iPhone
It is possible to regain control of your device, and it isn’t that difficult. To do this, you need to contact Apple technical support. The best way to do this is to call (800) APL-CARE (800-275-2273). Of course, you can also write to the chat, but you will obviously tell more with your voice, and therefore you will get faster help.
But, before you call, you have to prepare a little: find a box from the locked device and preferably a receipt. You will probably be asked to confirm your identity. So it’s better if you have both.
After you outline your situation to the tech support person, they will send you an email that you dictate. In response, you will need to send a photo of the receipt indicating the purchase, as well as a picture of the back of the package with the serial number printed on it.
The consideration of your application will take no longer than a week, but as a rule, the answer is given in a day, a max of two days. But under no circumstances, don’t transfer money to the fraudsters. They can’t do anything worse than what they have already done.